Key Takeaways
- The stolen ETH was laundered through Tornado Cash.
- The victims were lured by the offering that they could swap a malicious fake token for UNI.
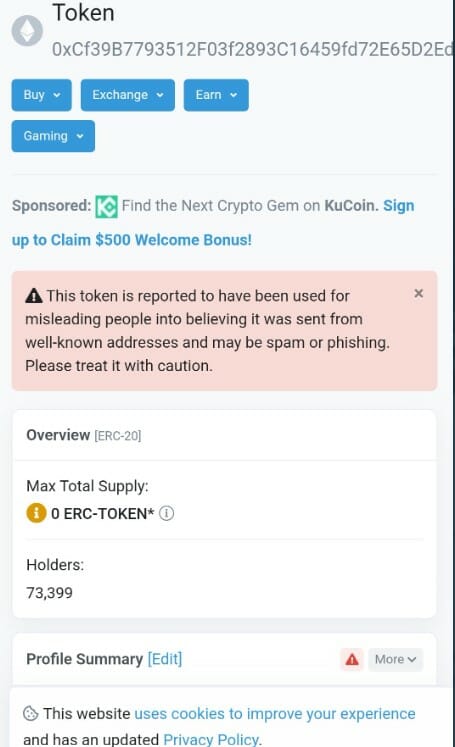
- Over 70,000 addresses had been sent malicious ERC-20 tokens to steal their assets.
- Uniswap team states the attack was part of a phishing campaign and not a protocol hack.
Uniswap V3 Liquidity pool gets hit by a phishing campaign that stole roughly 3,278 ether worth of NFT positions or approximately $3.5 million. The phishing attack detected Monday was first brought to attention by Metamask security researcher Harry Denley who tweeted that 73,399 addresses had been sent malicious ERC-20 tokens to steal their assets.
Later Binance CEO CZ took to Twitter to warn users of a “potential exploit,” stating that the users were laundered through crypto mixing service Tornado Cash. Soon after, he clarified with an update, sharing a text chain with the Uniswap team, who noted the attack was part of a phishing attack and not a protocol hack.
Uniswap protocol founder Hayden took to Twitter to reveal that it was a phishing attack that resulted in some LP NFTs being taken from individuals who approved malicious transactions.
How did the phishing attack happen?
Over 70,000 addresses were sent a malicious token called UniswapLP , under the false impression of a $UNI airdrop based on their LPs. The victims were lured by the offering that they could swap the malicious token for UNI(Uniswap’s token). The website would then read sensitive information and steal funds from wallets.
To do so, the malicious contract polluted the event data so that block explorers index the “From” as the legitimate “Uniswap V3: Positions NFT” contract. Following the user seeing that “Uniswap V3: Positions NFT” have sent them a token (without knowledge of the event pollution attack), clicks on the token.
The token name directs them to a website(domain “/uniswaplp.com”,) that copied Uniswap rebranding. The curious users would connect their wallets in the website, which would instead send the users’ address and browser client info to the attackers’ command center, thereby draining cryptocurrency from their wallets.
Reportedly, the phishing campaign mainly targeted native tokens (ETH), ERC20 tokens, and NFTs (primarily, Uniswap LP positions). Uniswap’s liquidity positions on V3 are represented as NFTs, which enable users to utilize them as collateral to receive a loan paid out in stablecoins and blue-chip assets. According to the crypto community, the total loss may spike above $9 million as more information arrives.
The price of UNI faced minor setbacks after CZ falsely described the phishing attack as “potential exploit”. The Binance CEO’s initial statements coincided with a fall in the UNI price, which fell to a 24-hour low of $5.34. Following the clarification, the price of UNI has recovered and currently stands at $5.57











