- A popular Taiwanese pop star, Jay Chou has lost more than $550,000 worth of top-notch NFTs.
- The scammers stole an NFT from the Bored Ape Yacht Club collection.
Yesterday a popular Taiwanese pop star, Jay Chou has lost more than $550,000 worth of top-notch NFTs. He lost the NFTs after falling victim to a phishing scam. The scammers stole an NFT from the Bored Ape Yacht Club collection.
The stolen NFT from BAYC was given to him by famed Taiwanese singer Jeffrey Hwang (aka Machi Big Brother). He also dropped one NFT from Mutant Ape Yacht Club and two from Doodle. One of Asia’s biggest stars confirmed the theft in an Instagram post yesterday. Chau claims he initially mistook the theft for an April Fool’s joke before realizing he didn’t have access to his valuable NFTs.

BEOSIN has always been concerned about the security of NFT and has sought to provide appropriate solutions. BEOSIN used Beosin-Trace immediately after Jay Chou’s NFT theft to conduct an on-chain tracking analysis of the stolen NFT.
Timeline of jay Chou’s NFT Theft
According to BEOSIN timeline and path analysis of Jay’s stolen NFT on 2022-04-01 at 3:07:29 the phishing attacker transferred BAYC #3738 NFT from Jay’s wallet address beginning with 0x71dE2148051A7544A082178B3e6A6DD1E0fE97a1 de2 to his own wallet beginning with 0xe34F004BDef6F069b92dc299587D6c8A731072Da.
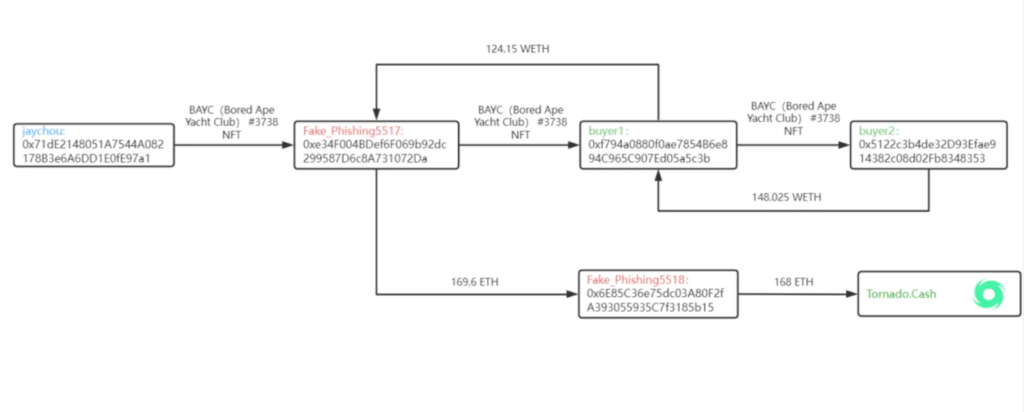
On 2022-04-01 at 3:44:49 the attacker sold BAYC #3738 NFT to buyer 1 via LooksRare with the price of 130 WETH. After deducting the transaction fee, transferred the profited 124.15 WETH to the attacker’s own wallet starting with 0xe34F004BDef6F069b92dc299587D6c8A731072Da.
On 2022-04-01 at 3:52:57 the buyer 1 sold BAYC #3738 NFT to Buyer 2 via LooksRare for 155 WETH and transfers the profited 148.025 WETH (deducting transaction fee) to Buyer 1’s wallet starting with 0xf794a0880f0ae7854B6e894C965C907Ed05a5c3b.
On 2022-04-01 at 3:58:28 the phishing attacker started a money-laundering operation and transferred the stolen money obtained from the sale of BAYC #3738 NFT and the additional stolen money from the sale of 1 MAYC and 2 Doodles held by Jay, totaling 169.6 ETH, to another address under his control starting with 0x6E85C36e75dc03A80F2fA393055935C7f3185b15.
Then the attacker transferred 168 ETH to the mixer platform Tornado.Cash. Currently 1 ETH has been transferred to address 0x47CE0C6eD5B0Ce3d3A51fdb1C52DC66a7c3c2936; 10 ETH have been transferred to address 0x910Cbd523D972eb0a6f4cAe4618aD62622b39DbF; 100 ETH have been transferred to address 0xA160cdAB225685dA1d56aa342Ad8841c3b53f291.
As of 2022-04-02 at 14:23:00 BAYC #3738 NFT is still in Buyer 2’s wallet starting with 0x5122c3b4de32D93Efae914382c08d02Fb8348353.
BEOSIN will use Beosin-Trace to continuously monitor the incident’s progress and will be the first to notify you if there are any new developments.
- The URL of the phishing website(mutantshiba.army) is currently inaccessible. According to BEOSIN analysis, they have checked the IP results of the domain name: 172.67.148.234, 104.21.11.108, both are Cloudflare and they are temporarily unable to find the real IP. Some of the WHOIS information of the site are as follows:
- Created at 2022-03-19 05:48:33
- Expired at 2023-03-19 05:48:33
- Updated at 2022-03-24 05:49:04
The registrant of the website belongs to the organization Anonymize, Inc. The country is the US and the domain name of the service provider is Epik, Inc.
BEOSIN has recommended Chou that users can apply to investigate the information related to KYC credit card payment of the domain service provider to track down the hacker’s true identity information, but this is not easy and may require the assistance and support of relevant judicial procedures. Finally, they said that BEOSIN hopes that Jay’s stolen NFT can be recovered.










