An unknown attacker is stealing the assets listed on Opensea from the owners of high-value NFTs. Either the new Opensea contract was compromised, or users were subjected to a phishing attack.
A Twitter user named Eric Tweeted that “Active NFT exploit going on with many wallets being drained. A contract was deployed here 28 days ago and the exploiter is using it to drain certain accounts. Not sure what’s going on but go revoke NFT approvals to be safe.”
As of writing this, the attack seems to be over. Outgoing transactions on the attacker’s account and the attack contract have been suspended for more than 30 minutes. The attacker currently has 641.5 ETH in liquid assets and a large number of high-value NFTs, including 17 Azuki, 3 BAYC, 2 Cool Cats, and 2 Mutant Ape Yacht Clubs. The attacker also stole the racial slur ENS’s name.
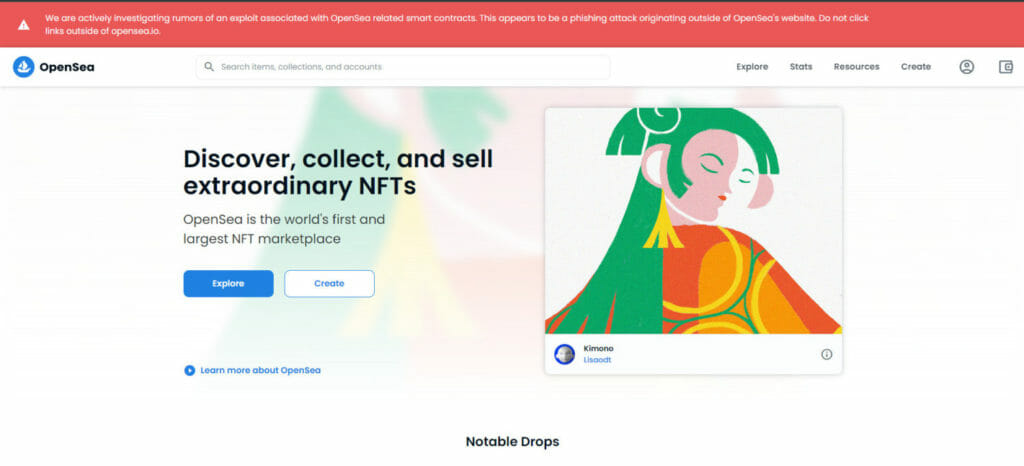
OpenSea Tweeted that “We are actively investigating rumours of an exploit associated with OpenSea related smart contracts. This appears to be a phishing attack originating outside of OpenSea’s website.”
The situation is changing, but it appears that users have fallen victim to a phishing scam for the time being. The attacker most likely struck now because the phished listings are about to expire as a result of the OpenSea contract migration.
So far, the attacker has made off with 680+ Ether. Their Opensea activity is out of this world. OpenSea has currently taken that activity page down. Bored Apes, Mutant Apes, Azukis, mfers, FVCK CRYSTALS, Doodles, and pretty much anything else that isn’t nailed down is currently flooding into the wallet and being sold at or below the floor.
Rumours are wallets are getting drained. Hence people are suggested to go to Revoke.Cash. Revoke permissions for X2Y2 and OS if migrated. Because some people are saying it’s the New Opensea Migration and some people are saying it’s the X2Y2 contract that people are exploiting.
On Saturday around 10:50 p.m. Eastern, OpenSea CEO Devin Finzer tweeted that “32 users have thus far signed a malicious payload from an attacker, and some of their NFTs have been stolen.” He went on to say that the company is “not aware of any recent phishing emails that have been sent to users,” and that a bogus website could be to blame.
The rumoured exploit, according to PeckShield, was “most likely phishing” – a malicious contract hidden in a disguised link. The same mass email about the migration process was cited by the company as one of the possible sources of the link. Click here to get the list of NFTs stolen in this phishing incident.
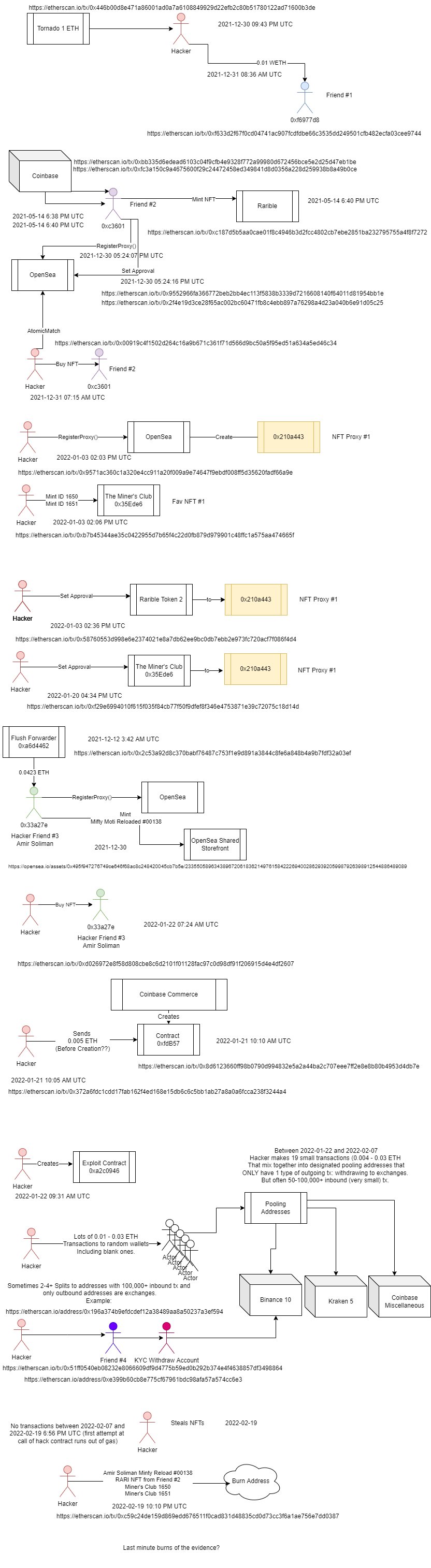
According to a Twitter user named charliemarketplace.eth the attacker tornado’d into a fresh wallet 12/30, made a weird contract call on Jan 22nd to OpenSea’s contract (etherscan down of course, so I can’t investigate calldata) and now he’s pulled 18 (and counting) batches of NFTs.
Further Tweets by him said that it looks Like OpenSea has tagged Amir Soliman as a suspect. That was fast!! His Tweet further stated I can provide PDF copies of this so you can review tx hashes as well. The Coinbase linkage is most obvious, but there’s more. He has uploaded the pdf here.