On March 24 PeckShield informed the community that the Unverified PYE (PYE) smart contract is exploited in a flurry of TXs leading to the loss of ~$2.6m. The exploit is possible because of the lack of “k invariant verification” in the swap() routine. The transaction Hash is 0x3823a6841b025e871928306de1805d994366bc8d283494a8f15d0884e67fe2b1.
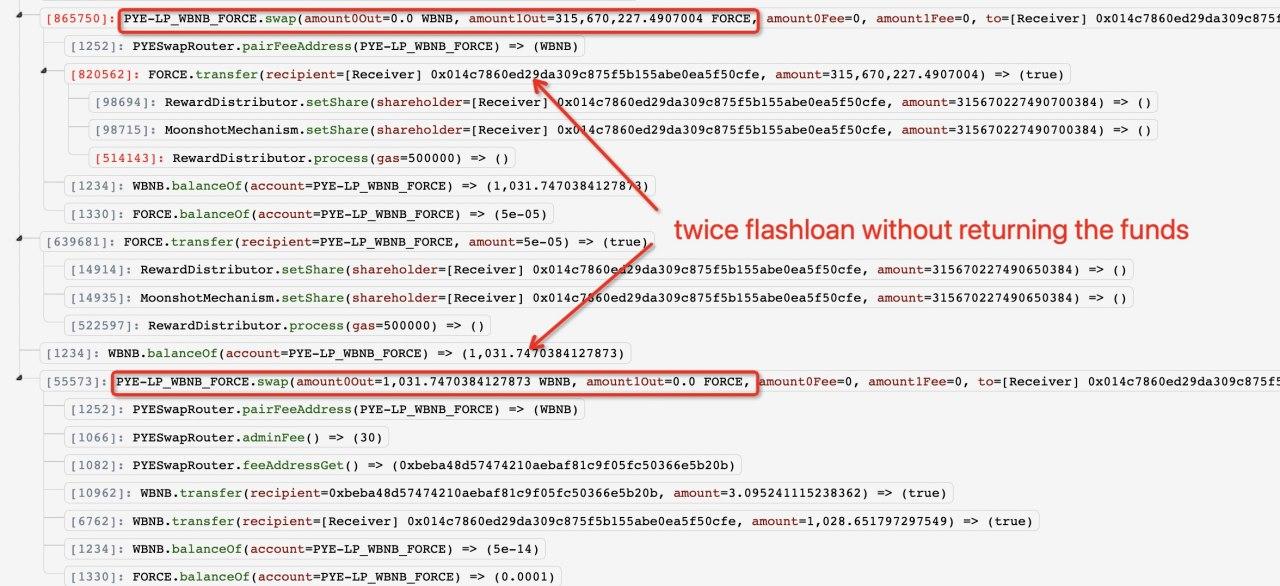
Today PeckShield Tweeted that PyeEcosystem may need to explain why the caller verification is removed in the PYESwapPair. Otherwise, this is an inside job! Note the lack of caller verification is the key behind the hack (anyone now can drain the LP liquidity).
In response to PeckShield PyeEcosystem replied Hello PeckShield We identified this earlier in during our internal investigation and communicated it with our community as well. As stated we are working directly with CertiKTech on a full investigation on this. Feel free to message if you have any direct questions for us.
At the time of writing, there was no official announcement by PyeEcosystem about the exploit.










