Key Takeaways:
- Today EarnHub informed people that the EHB Staking pools have been compromised.
- A hacker was able to exploit their contracts and steal most of the tokens in certain pools, then sell them, draining their LP.
- They informed people that if they are staking in the step pool, then they should unstake their tokens now.
- They even informed people that they have discovered a way to turn off buys and sells by using the anti-whale mechanism in the function and all trading is paused right now.
- The hack that happened today pulled out all of the tokens from the staking pools.
Today EarnHub informed people that the EHB Staking pools have been compromised. A hacker was able to exploit their contracts and steal most of the tokens in certain pools, then sell them, draining their LP. They even told their users that if they are staking in the step-pool, then they should unstake their tokens now. They further said that they are looking into it, and will share a time for a VC in which we’ll discuss what happened and a plan of action.
They further released a post-mortem explanation of the contract exploit that allowed the hacker to take tokens from the staking pool and sell them. They have asked people to join them on Telegram to discuss their next steps. They will even record it. They even said that in their Telegram they will have a vote to discuss the options proposed in the voice chat today.
They even informed people that they have discovered a way to turn off buys and sells by using the anti-whale mechanism in the function and all trading is paused right now. The hack that happened today pulled out all of the tokens from the staking pools. It is not possible to unstake.
According to their post mortem report an attack, causing all of EarnHub staking pools to be drained happened today (02/07/22) at 9:45 am PST. The exploit itself wasn’t hard to execute. The exploiter’s address is 0x3d98aee279c82d8178b87d9d4dc442d65224dacc. Attacker contract A is 0x89011932e486Fc3548f82c279Eb502BA7B4aD55F and contract B is 0xF7ACFA1cE0e235E7072fA76bD0DC3c3E519BDFe5.
As per their post mortem report, the logic error was in the makeHop() function. The makeHop() function allowed shareholders to shift their funds through different staking pools in a gas-efficient manner. This feature was intended to be implemented on the next dApp update, however, it’s been around for about 1 month on the contract side.
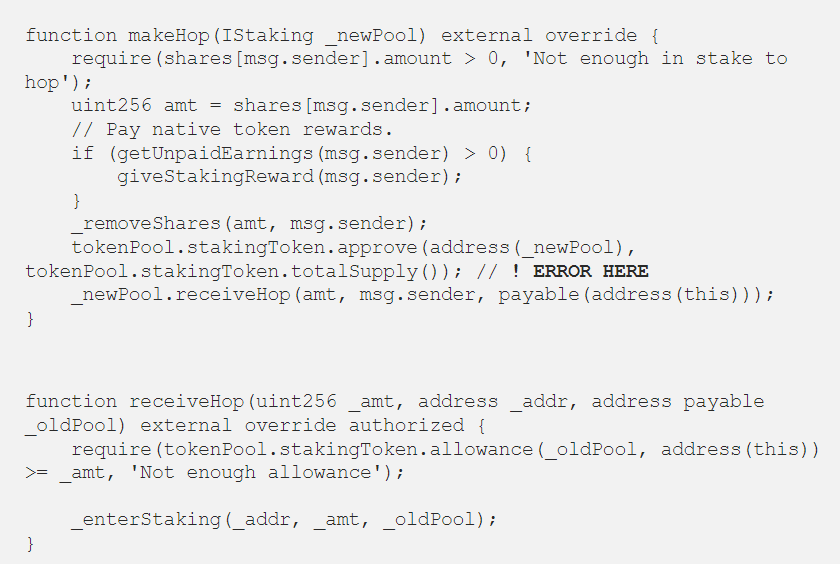
The issue is marked as an error here in the above image which assumes that there can not be a malicious smart contract on the pool that is called on receiveHop(_pool). By approving the totalSupply to the new pool, Contract B was able to have the allowance to spend the staking contract tokens. This basically means they were able to withdraw them from the staking contract at a whim once that initial setup was made. The attack started at 9:45 am PST and it was conducted as shown in the image below.
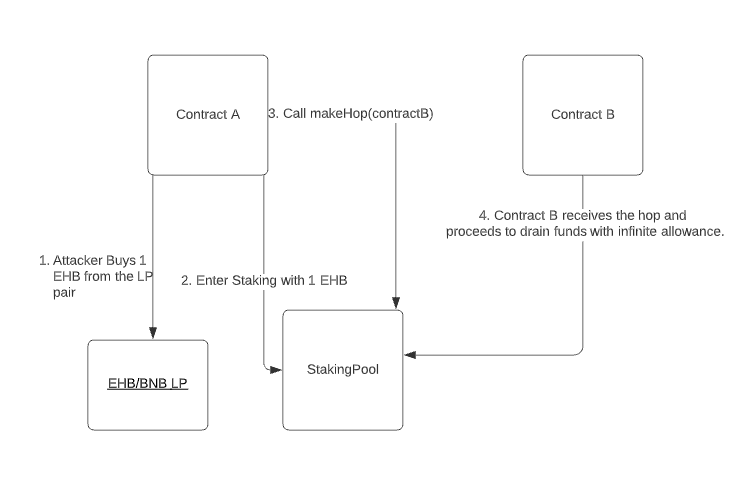
As one can see the attacker created contract A and contract B as the “leecher” contract. The attacker contract then proceeded to buy some EarnHub, stake it, and make it hop to the leecher contract. After receiving the hop, the contract was able to drain the funds from the staking contract by just using the transferFrom() function repeated times.