Indexed Protocol Hacked Updates | This article is a follow up to yesterday’s article of a $16 M hack of Indexed Protocol. Further, as of this morning the team at Indexed Finance and Laurance Day, they are very close to identifying the hacker and have presented him/ her/ them with a deadline of 17th October to return the funds.

Indexed Protocol Team has seen a remarkable improvement in determining the identity of the attacker. The team is in connection with Code 423n4, Binance, and Coinbase. Code 423n4 is an organization to find flaws in the smart contracts of decentralized protocols.
Timeline
- 06:05 BST, October 16th: Attacker is Identified and issued an ultimatum.
- 01:50 BST, October 16th: A complete Twitter thread is posted on Indexed Protocol’s official Twitter account explaining the current thoughts of the core team regarding the current state of affected tokens and the path forward. Indexed Protocol has also announced a $50,000 bounty for information about stolen funds.
- 18:29 BST, October 15th: Indexed Team has found a Reddit account with the same username which requested a Kovan testnet Ether to the attacker’s account.
- 01:54 BST, October 16th: Indexed Team found a frontrun transaction after a closer inspection. Check out this transaction on EtherScan.

History of Attacker’s Identity
Team was Contacted by Attacker Before the Incident
- The team has communicated with attackers several times before the incident.
- September 15th: Team was approached by a Discord user UmbralUpsilon, i.e. BogHolder#1688. They asked the team about various parameters in the TWAP oracle. Although this was not part of the attack, but attacker used this to start the conversation. The team answered these queries since every component of the protocol is open-source. The team always answers the queries of users in the spirit of open-source collaboration. The team then asked the reason for such a question. Then attackers told the team that they were creating an arbitrage bot for the pools.
After the Attack
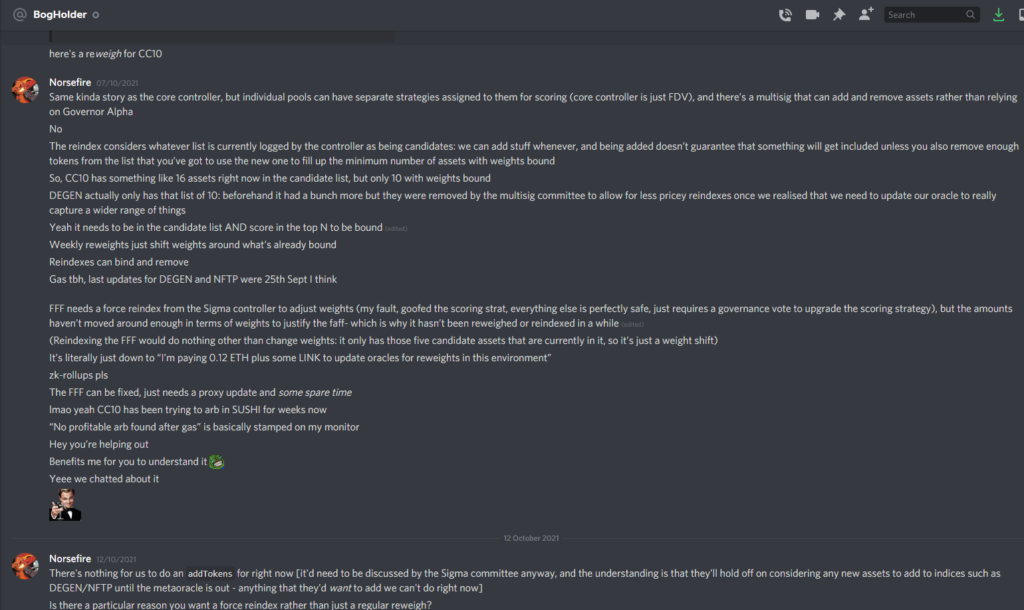
- Dillon Kellar and Laurence Day were the core team members who were involved in the conversations with the attacker. They found that the user’s side of the conversations is deleted completely.
- Here are the screenshots shared by Laurence of the discord chats with the attacker.
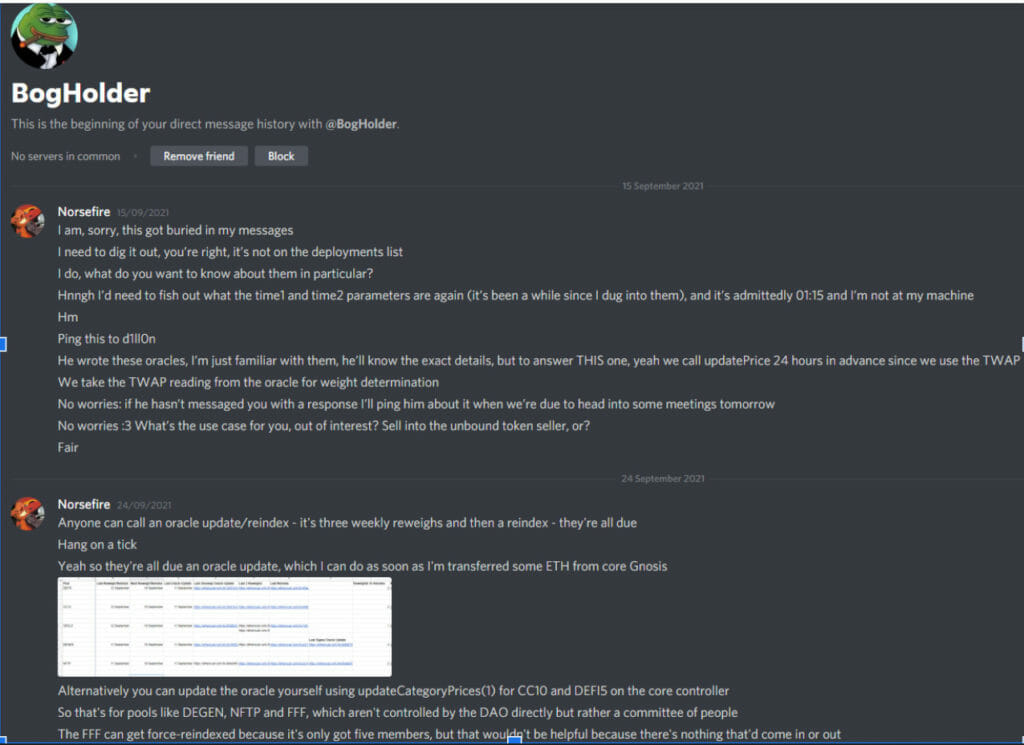
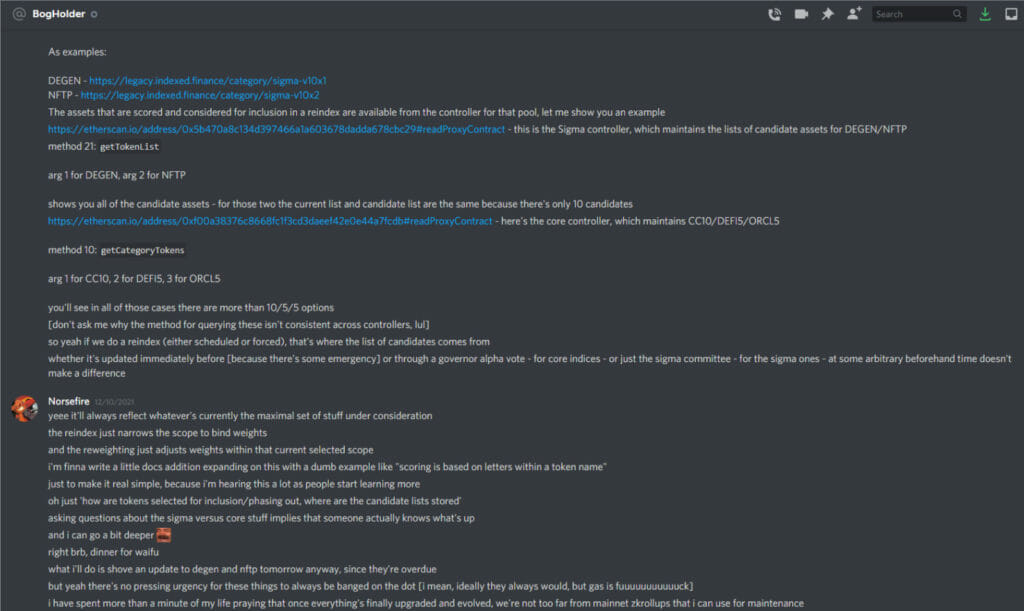
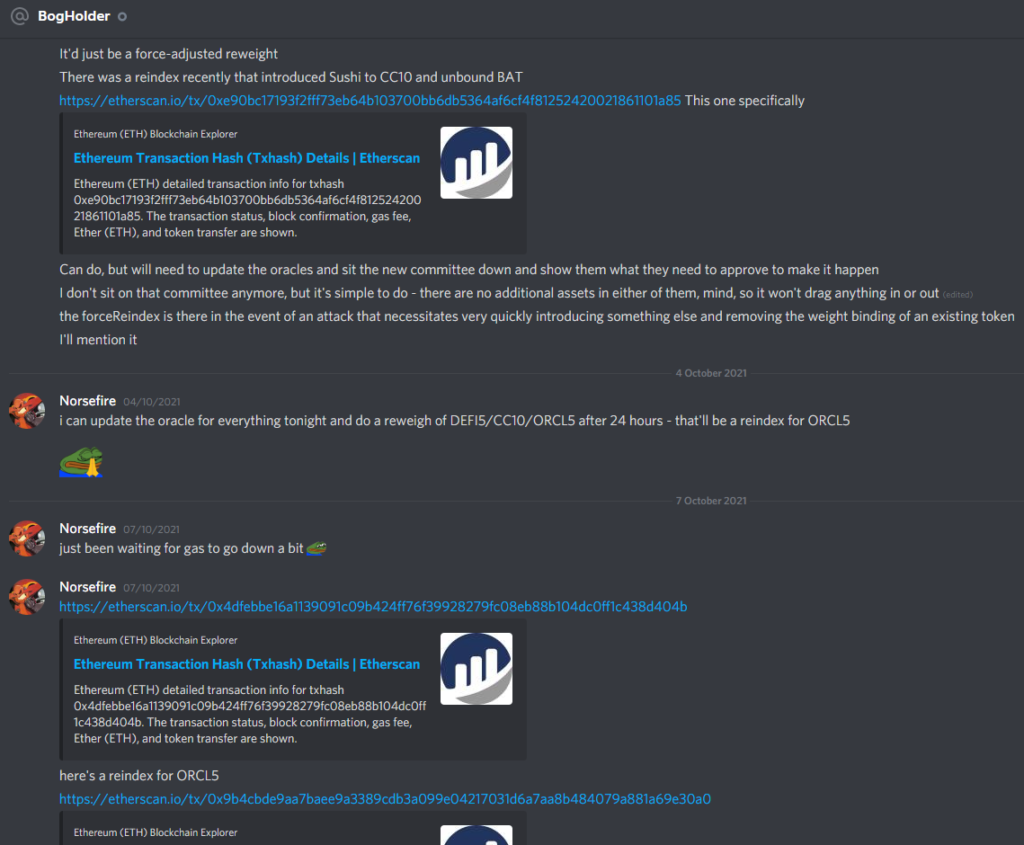
Pascal Caversaccio has made the team aware that the attacker has requested some Kovan testnet Ether via Gitter, using the Twitter account ZetaZeroes. The team has reached out to attackers via Gitter.
Here is the screenshots of chats with the attacker shared by the team.
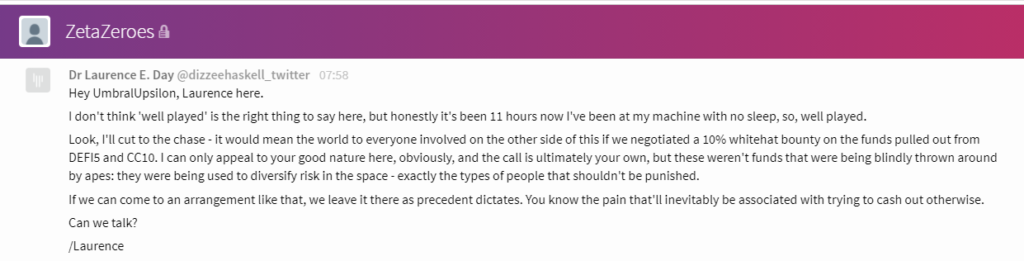
Team has reached out directly to attacker(0xba5ed1488be60ba2facc6b66c6d6f0befba22ebe) with message.
The team has directly told the attacker that: You’re clearly incredibly skilled: this is something that has been overlooked for ten months in production, and you’re the only one that found it. While it would have been so much more productive for you to instead choose to work with us: be the antihero of this story rather than the villain. Take a 10% whitehat, and save a lot of people the effort of engaging law enforcement.
Effect on the Indexed Protocol
- Damage by attackers is not just financial, but developers are receiving death threats.
- $16M of assets that the attacker stole are in this address.