Key Takeaways:
- PeckShield Inc. informed people that the $FLOAT price oracle used in FloatProtocol is manipulated to drain about 350ETH value of funds from the affected pool.
- According to FloatProtocol, their RariCapital pool just experienced effects from a weak oracle and only primarily protocol-owned liquidity has been affected by this incident.
- Float Protocol Pool 90 on RariCapital pool suffered effects from a lack of liquidity in the Uniswap V3 FLOAT/USDC oracle which led to severe price manipulation.

This morning PeckShield Inc. informed people that the $FLOAT price oracle used in FloatProtocol is manipulated to drain about 350ETH value of funds from the affected pool. Before PeckShield FloatProtocol Tweeted about the incident and informed people about it. According to FloatProtocol, their RariCapital pool just experienced effects from a weak oracle. Primarily protocol-owned liquidity was affected by this incident.
Float Protocol Pool 90 on RariCapital pool suffered effects from a lack of liquidity in the Uniswap V3 FLOAT/USDC oracle which led to severe price manipulation. FloatProtocol released the post mortem through the Thread on what and how it happened.
According to the post mortem released by them, what actually has happened is that in the past week, the FLOAT/USDC UniV3 pool had ~$1M withdrawn, leaving ~$550k FLOAT/USDC in Uniswap V3. This combined with a narrow band allocation and the increasing price of $FLOAT leads to the useable liquidity being insufficient to protect from oracle manipulation.
The vast majority of FLOAT (>80% of FLOAT) is in liquid circulation in various AMMs due to reward incentives and bonding. The liquidity is as follows:
- FLOAT/ETH sLP ($1.8M Multiplier Pools)
- FLOAT/ETH sLP ($300k Onsen)
- FLOAT/ETH UniV3 ($320k)
- FLOAT/USDC UniV3 on G-UNI ($567k as of now) in a band [$1.16, $1.74]
The Rari 90 pool used the FLOAT/USDC Uni V3 as an oracle for FLOAT; while BANK used a SushiSwap LP oracle and was unaffected and was not impacted by this manipulation.
The attacker brought in >47 ETH via Tornado Cash and deployed an orchestrating contract. Through the contract they swapped 47 ETH -> 129,447 USDC -> 77.5k FLOAT. This brought the vast majority of FLOAT out of the pool and it dramatically increased the price within the FLOAT/USDC pool. The attacker then waited for 2-7 minutes for the time-weighted oracles to shift the price.
At this point, they were then able to deposit FLOAT into Rari Fuse at a vastly increased rate and borrow other assets, before selling the FLOAT back into the Uniswap V3 pool to return the price. According to the postmortem, the orchestrating contract still contains 250k USDC and 5 FLOAT.
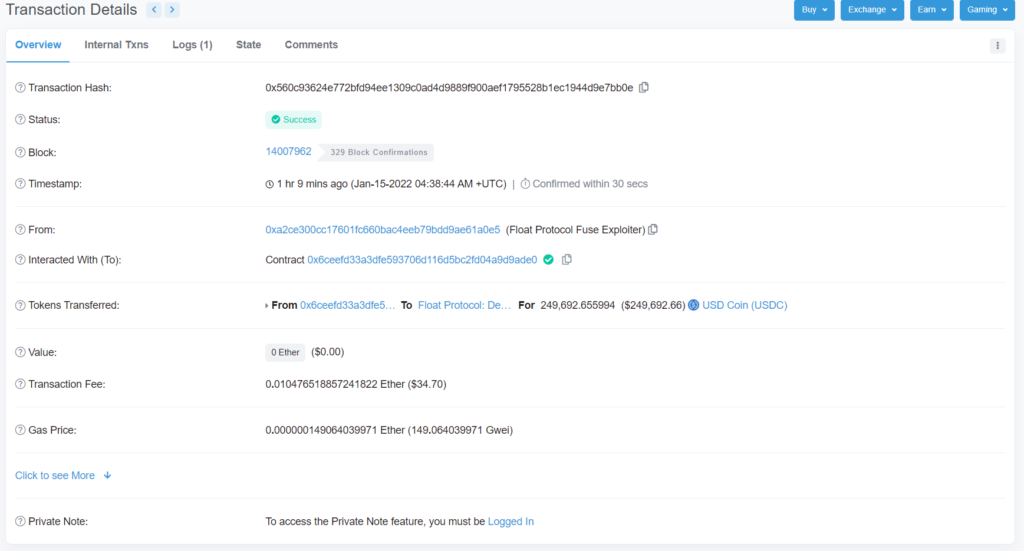
They further wrote that at the time of the attack, they had not yet incentivized deposits and BANK deposits were not impacted and they could not be borrowed. The depositors primarily impacted were Float Protocol’s treasury diversification funds, FRAX AMO, and FEI PCV deposits. According to them, they calculated that there was 1 depositor of $25k DAI in user funds lost at this time, but they are still collecting further information for a follow-up proposal.
However, there is a light of hope after all as the attacker who hacked FloatProtocol returned $250K.
Also, read