Yesterday Fantasm Finance Tweeted and informed the community that there is an urgent announcement people should redeem their XFTM. FTM collateral reserve has been exploited, there is still 1,820,012 FTM pool balance remaining currently for redemption. The Exploiter address is 0x47091E015b294B935BAbDA2d28aD44e3Ab07ae8D. It also said the community to exit from liquidity pools.
Fantasm Finance further updated the community. According to their Tweet, some of the FTM collateral reserves has been whitehacked. They further notified the community that “we apologize for the exploit event which just happened. A Post Mortem with compensation options will be published by tomorrow. We are analyzing the exploit right now. Most sincere apologies once again.”
According to our sources, the attackers were able to mint way more $XFTM tokens than they are supposed to and has swapped all of the tokens to ETH. Total loss is around ~$2,700,000 (1,000 ETH). The attacker deployed an unverified contract 0x944b58c9b3b49487005cead0ac5d71c857749e3e. In the first tx, the attacker swapped $FTM to $FSM and called mint() function in contract 0x880672ab1d46d987e5d663fc7476cd8df3c9f937.
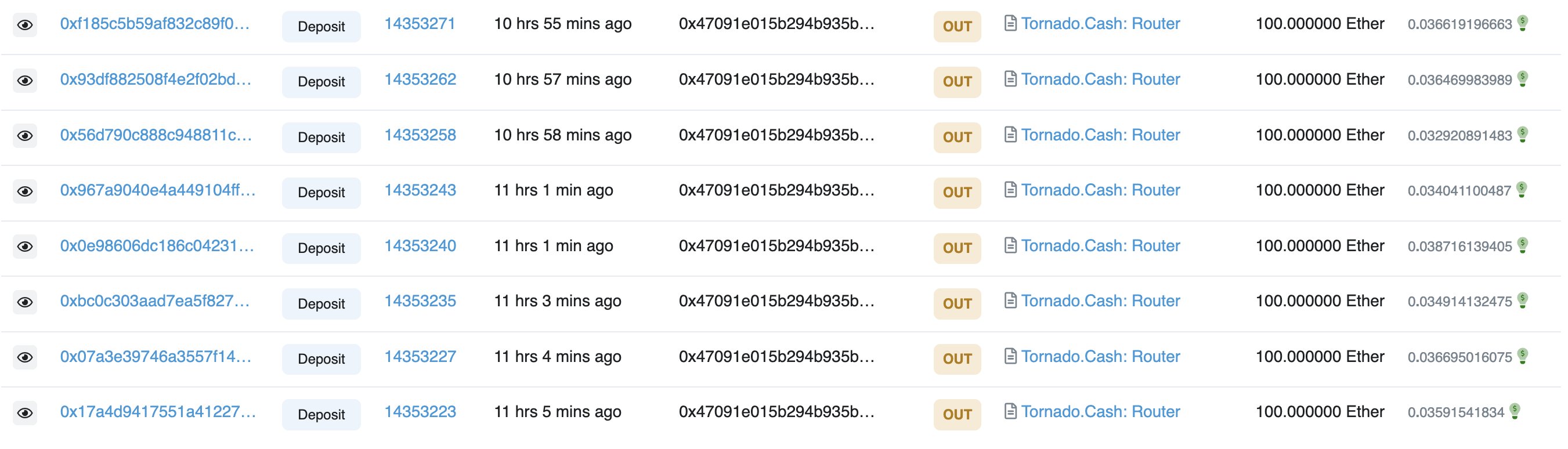
The attacker called the collect() function and collected way more XFTM tokens than supposed to. The attacker repeated these steps several times. At the time of writing the attacker has 1,007 ETH into TornadoCash. The address is 0x47091E015b294B935BAbDA2d28aD44e3Ab07ae8D.
According to the Post Mortem released by Fantasm Finance, the attack started at approximately 02:00 p.m. UTC. They have been made aware of suspicious transactions related to the Fantasm protocol which resulted in a loss of $2.62M. According to their analysis, the Exploiter gets funds from BNB Chain via Tornado Cash. The transaction hash for this is 0x11407dd11dd028cfefdb24c9bde9163b4d10e3338e62c74ae2f5f3c2ec863133 and 0xeffe3e64b2df1e80d5282a55bd12a7e89cd088616d85274bb1589b3b96526f28.
The exploiter then swaps BNB to USDC via Pancakeswap. The transaction hash for this is 0xe47bd66738fd6721817ebc68cfdfde19d860330cc8b84bdf6761a3f1957ef188. The exploiter then bridges USDC to Fantom via Celer Bridge. The transaction hash for this step is 0x2b5f61778881958d98935cdfcbcb97a7de8405b1d059c931f02461776ad9e007.
The next step exploiter do is exploiter receive USDC from Celer Bridge. The transaction hash for this process is 0x39be07303cf562407c857d9b43077f99bd63ee46b1a95d5cfe5947ee3c106422. The exploiter then receives FTM from a faucet. The transaction hash for this process is 0x455f72c451743bccfd9800c43bb56fcdd72d135247335ce07946c36974f5b799. Then the exploiter swap USDC for more FTM. The transaction hash for this process is 0xed81960af5bba6cb7a48839ed9a6eed9b665cba4b9cfc1089603262e0082e9f2.
The Exploiter deploys a contract 0x944b58C9b3B49487005CEAd0ac5d71c857749E3e which will trigger the exploit. That contract exploited the error in Fantasm’s Pool contract where the developer missed the condition checking for the minimum amount of input FTM when minting XFTM.

This contract deployed by Exploiter repeatedly performs the following:
- Mint XFTM by input only FSM token without entering any FTM
- Collect XFTM token
- Sell XFTM token to FTM
- Buy more FSM and repeat the first step to get a larger amount of FTM
Eventually, the exploiter sold all his FTM for ETH and bridged these ETH to Ethereum, again via Celer Bridge. The total amount exploited is 1008.498875252390151 ETH (approximately $2,622,097). Exploiter used Tornado to siphon the stolen fund as mentioned in one of the above paragraph.
According to their Post-Mortem, their next step would be the main focus is the following tasks:
- Relaunch the protocol and launch the DAO.
- Perform the required steps needed to start refunding users.
- Work together with their auditor and confirm that the code vulnerability has been fixed.
- Reach out to external parties who can help them in investigating their forensic findings in more detail, such as getting in touch with Binance.
They encourage the attacker to reach out to the team and begin a dialogue for the return of users’ funds. They are impacting everyday users of DeFi and Fantasm Finance would like them to do the right thing. They will honour a bug bounty of 10% upon returning of funds.











